Securing Solr Deployments
The SearchStax Managed Search service takes the security of your Solr search infrastructure very seriously. We have built-in industry-standard security at the level of the cluster, network and SearchStax Managed Search dashboard.
- Industry-standard security at the Solr cluster level and network level.
- Environments secured with SSL out-of-the-box using Solr basic authentication.
- Custom firewall rules to lock down search infrastructure to a whitelist of IP addresses.
- Two-Factor Authentication (2FA) to increase log-on security.
- Regular quarterly scans to identify and patch any Apache Solr vulnerabilities.
Securing Solr
For production systems, secure Solr using Basic Authentication and an appropriate range of IP addresses
Warning: Site Search Security Settings
Components of Site Search will run on many different client computers, so the Solr endpoint cannot be shielded by IP Filtering. Solr’s IP Filter must be 0.0.0.0/0.
Therefore, Site Search enables Solr Basic Auth and creates two new Solr user accounts. Your SearchStax Admins will need Solr Basic Auth accounts of their own in order to connect to Solr.
Securing Zookeeper
SearchStax requires Zookeeper to be locked down by IP Filters.
See our Help Center page, How can I Secure Zookeeper? for additional information.
Securing Users
All SearchStax users log in using their business email address and a strong password. Each user may optionally enable two-factor authentication as a standard SearchStax feature.
Premium clients may request SAML-based single sign-on (SSO) using Microsoft Azure Active Directory as an add-on service.
Advanced Security Options
For our premium customers (Platinum, and Platinum Plus levels) who have high security requirements, we recommend a SearchStax Managed Search Private environment with VPC Peering.
Premium customers may also request at-rest encryption for their data files. Please contact us for more information.
Contents:
Cluster Security
You can lock down your clusters as described below.
Connecting to the Cluster
SearchStax recommends that you situate your application infrastructure in the same local network as your hosting provider (for example, AWS or Azure). Internal network security for these hosting providers is extremely high and eliminates any chance of a hacker potentially sniffing your network traffic.
If your application is hosted elsewhere, try to host it as close to your search infrastructure as possible. This can be done by choosing the Cloud Provider Region which is closest to your application. This improves both security and performance.
Solr Basic Authentication
You can optionally enable the Solr Basic Authentication Plugin through the SearchStax Managed Search Dashboard. This restricts access to your Solr dashboard and demands authorization for query requests and index updates.
Warnings: Effects of Basic Authentication
- Enabling/Disabling this feature will suspend service while it restarts
all of your Solr nodes.
- Once enabled, Solr will require a username and password for:
- Opening the Solr Dashboard.
- Making a query request (via the /select command).
- Adding records to the index (via the /update command).
- When disabled, Solr will delete all existing Solr users.
To enable the Basic Authentication plugin:
- Select the desired Deployment and click the Security > Auth option in the menu tree.
- Click the Enable button.
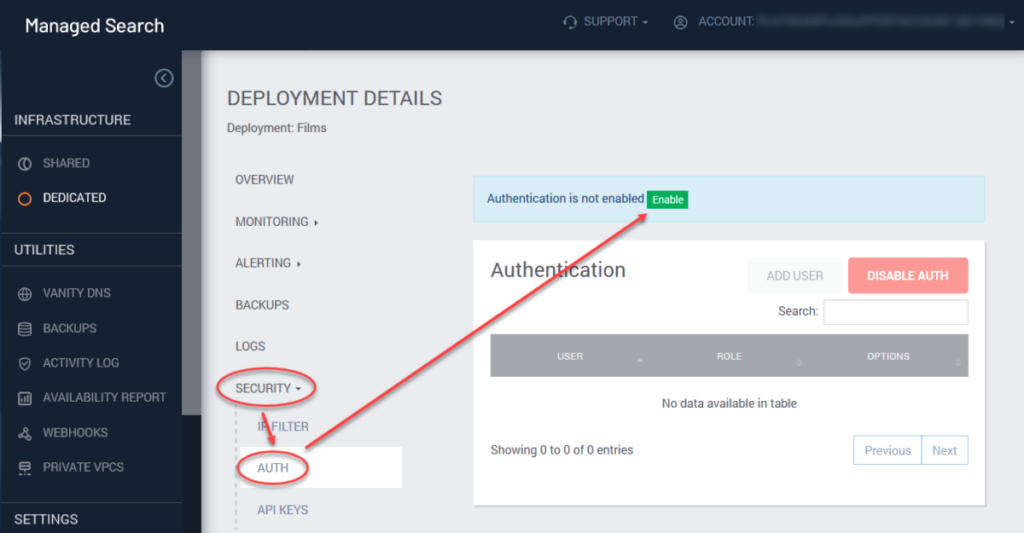
- Click the Add User button.
- Add a user, entering the username, password and role (see below). Click Add.
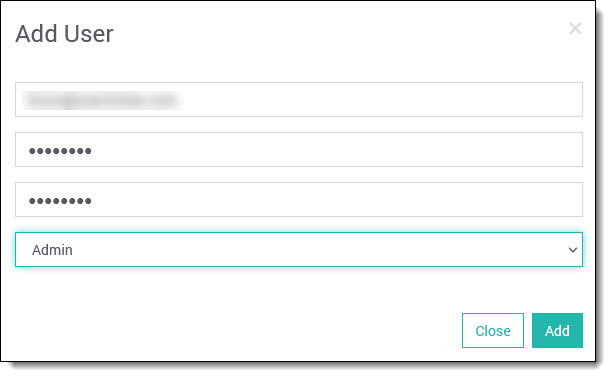
Note that Solr user accounts are independent of SearchStax user accounts.
To disable the Authentication and Authorization plugin, click on the Disable Auth button and confirm the action. Disabling Basic Auth erases all Solr users. (Again, Solr services will be restarted.)
Solr Basic Authentication provides four user roles:
- Admin users have full access to the views and tools of the Solr Dashboard. They can query the index from an external location using a /select command, and they can load new records into the index using a /update command.
- Non-Admin users can enter the Solr Dashboard but cannot view or make changes to the collections.
- Read users can query the index using /select.
- Write users can add new records to the index using /update.
- ReadWrite users can use both /select and /update.
| Role | Solr Dashboard | /select | /update |
|---|---|---|---|
| Admin | Full access to all features | ✓ | ✓ |
| Read | Limited access | ✓ | |
| Write | Limited access | ✓ | |
| ReadWrite | Limited access | ✓ | ✓ |
Using /select and /update with Solr Basic Auth
After enabling Solr authentication, your /select and /update interactions with
Solr must include the username and password of a Solr user.
For cURL, add the Solr credentials using the -u 'username:password' parameter.
If your search application doesn’t use cURL, your <Solr HTTP Endpoint> changes
from https://machine... to https://user:password@machine...
If you are trying to use Basic Auth credentials from PowerShell, see Basic Auth Credentials in PowerShell.
Connections to Zookeeper remain unchanged.
IP Filtering
When Solr or ZooKeeper become Unreachable
Most IT departments and ISPs issue IP addresses using the Dynamic Host Configuration Protocol (DHCP).Your workstation’s IP address can change without warning. When it does, you’ll have to update your IP filter settings.
Cannot add another IP Filter?
There is a maximum number of IP Filters per deployment. See Cannot add another IP Filter for more information.
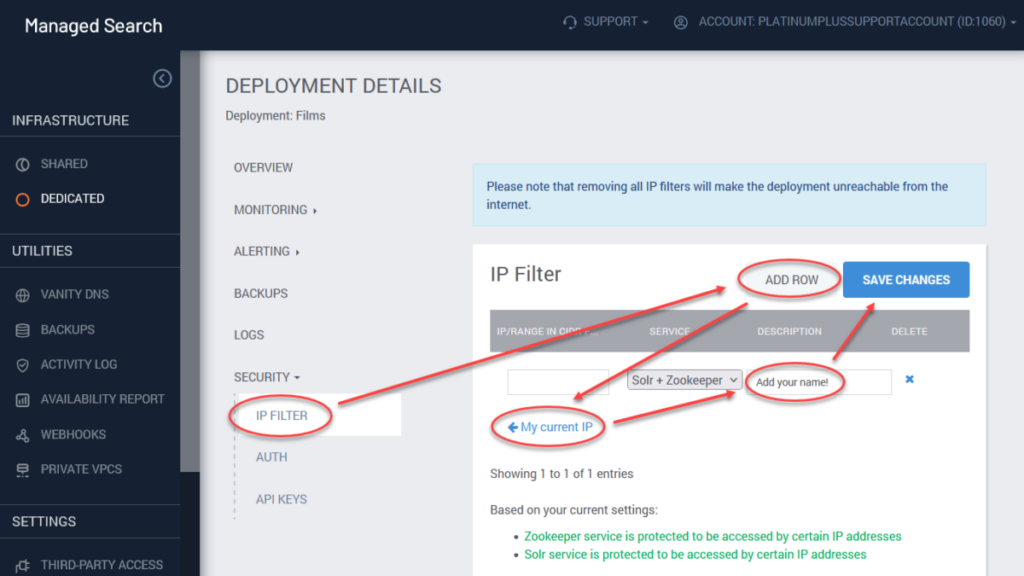
You can limit access to a Solr deployment to a list of IP addresses using the Security > IP Filter menu.
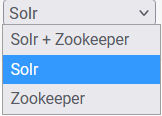
You can configure access for Solr+Zookeeper, Solr, and Zookeeper endpoints separately.
The addresses are expressed in IPv4 format, using the familiar dot-decimal notation. Ranges are specified using Classless Inter-Domain Routing (CIDR) format.
CIDR notation can be daunting, but note the following three examples of typical CIDR rules:
- 0.0.0.0/0 This rule permits unrestricted access to Solr. Any IP address whatsoever may connect, regardless of other filters you have added to the list. (SearchStax Managed Search will refuse to accept this value if you try to enter it for Zookeeper.)
- 64.118.123.159/32 This rule permits a connection from exactly one IP address.
- 64.118.123.0/24 This rule allows Solr access from any of the 256 IP addresses on a subnet.
The /n at the end of each rule is called the prefix length.
To limit access to a specific IP address or IP address range:
- From within a Deployment’s details page, click on the Security > IP filter option.
- Click on Add Row.
- Add a specific IP address in the appropriate field. Note that SearchStax Managed Search can detect your computer’s IP address. Click My current IP to enter it automatically.
- Select a service you need to limit access to (Solr+Zookeeper, Solr, or Zookeeper).
- It is a Best Practice to enter your name or email in the label field.
- Click Save changes.
To remove a filter, click on the X button and then Save changes.
API Keys
The Security > API Keys menu option exposes a table of the deployment’s API Keys.
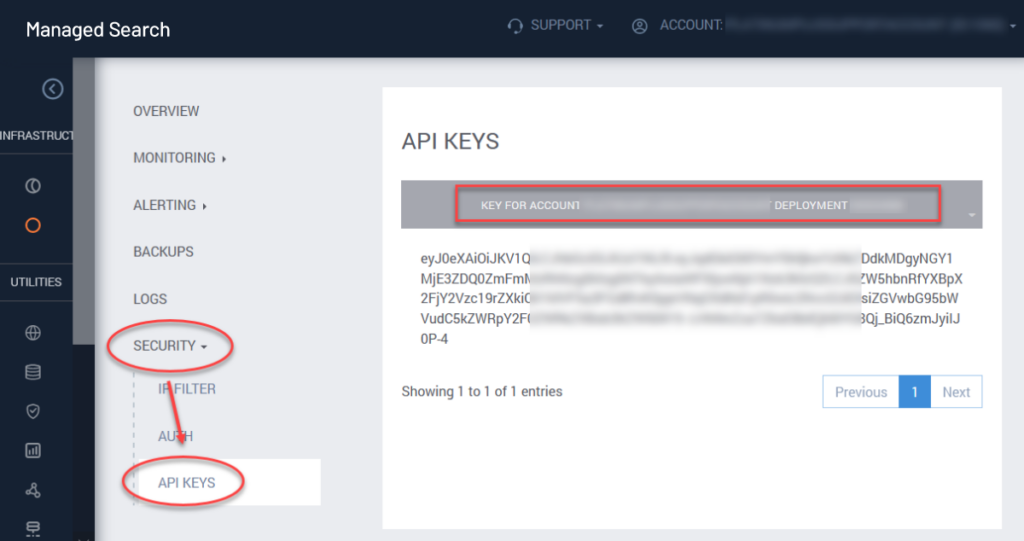
Ease-of-use Feature
Note a subtle ease-of-use feature here: This is the only place in the SearchStax Managed Search Dashboard where you can mark/copy the API Key, the Account Name, and the Deployment ssID Number. These values are heavily used in the SearchStax API.
SearchStax User Roles
Each SearchStax account is restricted to the Owner of that account plus any SearchStax users who have been granted access to that account by the owner. The additional users may be limited to specific roles at the Owner’s discretion. See SearchStax User Roles.
Activity Log
The SearchStax Managed Search activity log provides you with a list of all user actions within your account, including those of the SearchStax Support team. The list consists of a User column including email of the user who performed the logged change, his/her role, Timestamp of action in UTC, Action itself, Action detail and IP address where the action originated.
Questions?
Do not hesitate to contact the SearchStax Support Desk.

